Uniken has developed a path breaking Secure Digital Platform, REL-ID™ – which delivers ubiquitous, rich multi-channel digital experience with military grade security to the customers, employees and partners of an enterprise. Uniken was founded by Sanjay Deshpande, Prakash Salvi, Nanjundeashwar Ganapathy, and Nilesh Dhande in 2003 in Boston, with the goal of setting up a world class innovation center. Uniken today boasts of 1M+ users on its platform.
Uniken has developed a path breaking Secure Digital Platform, REL-ID™ – which delivers ubiquitous, rich multi-channel digital experience with military grade security to the customers, employees and partners of an enterprise. Uniken was founded by Sanjay Deshpande, Prakash Salvi, Nanjundeashwar Ganapathy, and Nilesh Dhande in 2003 in Boston, with the goal of setting up a world class innovation center. Uniken today boasts of 1M+ users on its platform.
Introduction
Network communication is increasingly becoming more vulnerable to attacks. Most such attacks attempt to steal your personal details, card details (credit card or debit card), and various other information that can be put to malicious use, mostly to steal money. Whether it is Target, JPMorgan or banks that don’t wish to be named (obviously), our information is never safe enough.
These attacks target one or more of these elements in the network:
- Network
- System
- Application
Network
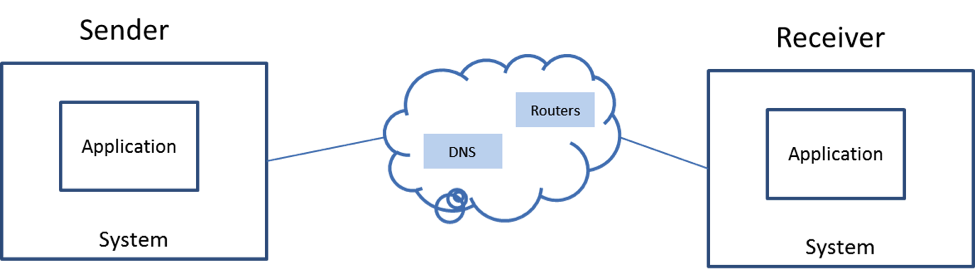
There are 2 kinds of network that we use. Internet is the ubiquitous network that allows us to connect to rest of the world. Intranet is the company-wide network that allows us to connect with rest of the employees in our organization. Security hazards in both these networks are slightly different
Internet
Internet relies on open standards and some special servers like DNS (to find the IP address from the server name) and routers (devices that keep the route map of entire Internet, sending network packets from a source towards the destination). They control the way network communications occur; compromising these special servers can compromise Internet (or a large part of it).
Intranet
Intranet normally assumes that all the nodes in the network are trustworthy, and it sends traffic to every node in the network so that the intended recipient can take it while others discard it. This poses a big threat if one of the machines is compromised; controlling one machine is enough for the attacker to control the network.
With cloud services (using Internet services to replace Intranet services) becoming more prevalent in organizations, the line between intranet and internet keeps blurring.
System
Communication happens between two systems on any network. If one of the systems (either sender or receiver) is controlled by a hacker, even a secure network cannot protect you from attack and theft. Malware and viruses are the primary ways systems get compromised, which can then take over a communication link or mislead your system into thinking it is communicating with X while real communication is happening with Y (X is real bank site, Y is fake site, stealing your bank customer id/username and password).
Application
A network and the system may be safe, but if the application you are using to do the communication (say the browser, or a Torrent application downloaded from Internet) is compromised, you are exposed to attack and theft. Given the prevalence of web applications, Browsers are increasingly becoming target of attacks. With the plug-in/add-in model that all browsers support, it is becoming easier for attackers to compromise the browser and thereby compromising the communication.
Securing the network must mean securing each of these elements of the network communication. This is what Uniken attempts to do for its customers.
Uniken Advantage
Uniken has developed a path breaking Secure Digital Platform, REL-ID™ – which delivers ubiquitous, rich multi-channel digital experience with military grade security to the customers, employees and partners of an enterprise. Through REL-ID, the end users enjoy a rich and secure digital experience across devices (Mobiles, Tablets, Laptops and Desktops) and platforms (Windows, Mac OS, Android, iOS and Windows Phone).
Currently, over a million end users, employees and partners of very large enterprises rely on REL-ID for a seamless and secure digital experience. These enterprises have witnessed online fraud being reduced up to 100%.
So what is REL-ID (Relative Identity)? In REL-ID communication, identity of a system is dependent on the other system it is communicating with. For example, if A and B need to communicate with each other, A’s identity is established relative to B, and B is identified relative to A (hence the name Relative Identity) – this identity is relevant only for A-B communication. Such an identity is established when A or B express interest in communicating with each other, thus creating a mutually authenticated channel for communication.
The Uniken Product
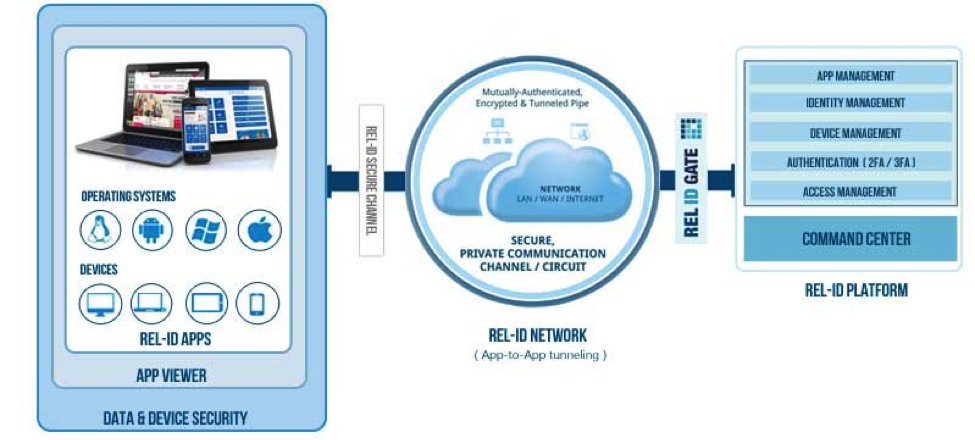
Through REL-ID, Uniken offers a unique and scalable way to create a secure private network. This is achieved through 3 sub-systems that Uniken deploys for its clients – REL-ID Apps, REL-ID Network, and REL-ID Platform.
REL-ID Apps
A REL-ID App is the client application that is responsible for providing a secure way to communicate to other clients or to the server. It serves 2 purposes in the REL-ID eco-system:
- Provide consistent experience to users in all device and OS configurations
- Provide a secure way to connect the communicating end points (client-client or client-server)
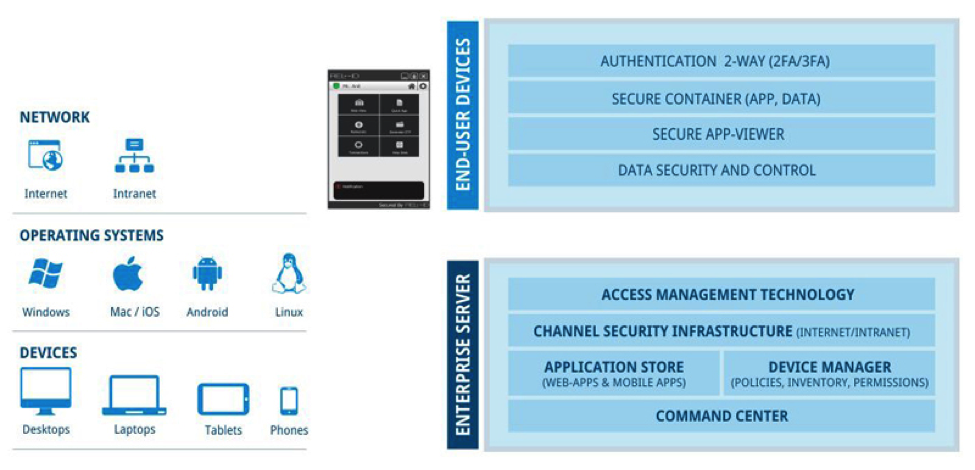
A REL-ID App has 2 parts:
- App Viewer – A native container of the application that is implemented differently for different platforms and abstracts the device-specificity. It enables creation of hybrid apps that use HTML/ HTML5 and Javascript for user interface and the APIs for accessing device specific functionality for security
- HTML5 app – A standard application (HTML5, JavaScript) that is hosted within the App Viewer
Given that they are hosted inside the App Viewer, these apps provide consistent experience running on all devices (desktops, laptops, tablets and mobiles) and all operating systems (Windows, MacOS, iOS, Android) thereby providing excellent customer experience.
For example, if a customer of a bank (who is a Uniken Client) has to avail of netbanking, customer will install a REL-ID app that allows netbanking, and transact through it. This app can be installed on any device.
REL-ID Network
As mentioned before, the REL-ID platform secures the network by creating secure point-to-point (application to application tunnel) connection between sender and receiver. Usually, such a secure connectivity is achieved through the use of VPN (Virtual Private Network) which is hard, costly to manage and deploy at a large scale in such point to point configuration. Within REL-ID, this is achieved without using VPN, using their patented technology.
Continuing with the above example, if the bank employee wishes to check his official mail from home using Outlook (an application that is not a REL-ID App), she can launch Outlook securely through the App Viewer and App Viewer will provide a secure connection to the Exchange Server hosted by the bank. The employee doesn’t need to use complicated procedures like RSA Token in order to achieve this.
REL-ID Platform
REL-ID Platform controls the policies, permissions and access management and authentication technologies. It ensures that REL-ID Apps and data is accessible only to authorized users through registered devices. It also hosts a REL-ID Store which is a library of pre-defined REL-ID Apps ready to be deployed through App Viewer.
Differentiators
Uniken differentiates its offering in 3 areas:
- Patented Military Grade Secure REL-ID Private Network – Supports Mutual and Multi-factor authentication, and state of the art App-to-App tunneling technology, enabling VPN-Less remote secure access through minimal infrastructure requirement. It creates a secure and private closed digital ecosystem, accessible to only authorized users and devices. Enabling this through VPN is a much more complex affair and impossible to be rolled out to large user base like retail banking customers
- Compelling Secure Digital Experience – Normally, highly secure applications/systems have meant poor usability (because of restrictions placed and the focus on non-functional goal like Security). However, Uniken has focused on making its apps highly usable in addition to highly secure.
- Quick Apps Framework – REL-ID Digital Platform comes with inbuilt secure private app store. These Apps are available not only on the Mobile Platforms (phones/tablets) but also on the desktops/laptops.
Development Process
Team
Overall product development + R&D team size is more than 80, with most of their core technology stack built in C/C++, with operating system and network programming skills. They also have a team for embedded systems, who work on creating special purpose secure appliances and devices. Apps are developed in standard HTML5 technologies.
They also have a Product Management team that works closely with the sales/marketing teams and the technology R&D and Product Development teams.
Process
Developing a security product doesn’t require a drastically different product development process or tools. They operate in an iterative 3-day development cycle.
One of the interesting aspect of their development approach (and which is different than other classes of software) is to create monolithic components rather than modular components (which goes against standard design principles of software development). This is to avoid creating multiple points of failure, which is critical to avoid from security perspective.
The features that are specific to the customers are built by separate customization teams. Customizations, when required, are small changes on top of the pre-built apps in the system, and can be typically done in a 7-day rapid development cycle. These are later analyzed (every month) and brought back in to the main product development roadmap if the sales/marketing team justifies doing so.
Even as a security product, usability is a very important aspect of their development process, performance is close second.
Market
Their target segment includes banking, insurance and defense, with the largest set of current customers coming from Banking, including one of the largest Public Sector banks in India.
Over past 2 years, REL-ID has been rolled out to over 1 million users and the count is rapidly growing.
REL-ID is being seen as the next generation security technology in the most difficult to penetrate security market of Israel. This technology has also been appreciated by Indian Defense & Navy where Uniken is supporting them in their security related requirements.
The information security market is projected to reach $67 billion (Rs 4.1 lakh crore) in 2013 and grow to $95 billion (Rs 5.9 lakh crore) by 2017, according to research firm Gartner.
On the security front, there are various players like Symantec, RSA, Vasco and on the network and virtualization technologies front, Cisco and Citrix. On digital experience front, Backbase and Adobe offer similar products.
However, none of these are scalable and unified/holistic to offer a secure digital platform especially when it comes to delivering secure digital experiences to consumers.
Roadmap
Their product suite is now fairly complete in terms of features and functionality. Over next 12-18 months, they are focusing on a few key areas:
- Make offering more broad across BFSI
- Go deep in India – Penetrate further in India (BFSI, Defense)
- Strategic expansion in other geographies – Execute opportunities in Israel (to build credibility by competing with other security companies in Israel), initiate penetration efforts in the US market.
As they expand, the key challenges are to manage the marketing and PR, and identifying the right partners in each of these markets.
The Road Ahead
Uniken has a vision that there will be a very large number of private networks in the world (built on top of public internet) using their technology, one for each group of people who want to communicate privately and securely with each other. In a way, this is counter to what Internet stands for (openness), but given the security and privacy issues mushrooming all over, this is a laudable vision. To be clear, this is very disruptive too: there are very large companies out there whose business models depend on the fact that they can ‘see’ the traffic generated through individual systems, be it a system in an organization, at home, on the road, in hospital, or anywhere else (think digital advertising, personalized search, etc.). These models will cease to exist (or have to be significantly rewired) if the vision of secure private networks come true.
Uniken is taking small but confident steps towards that vision. In next 12-18 months, they intend to have 5 million users on their system (from 1M currently). They are confident about their model of building in India and selling to the world, and their experience working with Indian PSUs (Banks, defense) has been great. Their global marketing efforts are underway, and they are establishing themselves as a potent force in the home of security products – Israel.
It is great to see hard-core technology product being made in India and we wish them all the best as they penetrate US and other big markets of the world.